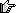One innocent day on Facebook, I received a message from a sketchily named character. Despite all appearances, Guest 7110 assured me that he was from the Meta Pro Team and delivered the unlucky news that "my fanpage is restricted from accessing". Woe is me!
That said, our numerated guest was never one to dwell on bad news. He happily informed me that I could verify my identity by opening 'support-media pages' and entering my username and password.
I wonder what he did with the other 7109 guests?
Being a curious fellow, I clicked the link to see what awaited there:
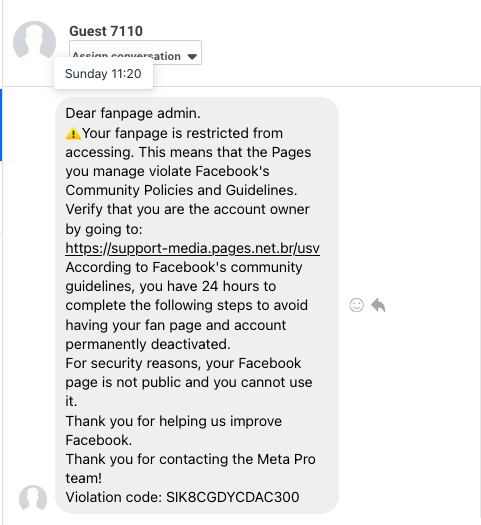
Login, sure you want to.
Ah, a login form! Seems very legit. And what happens if I enter any username and password? Alas, only errors.
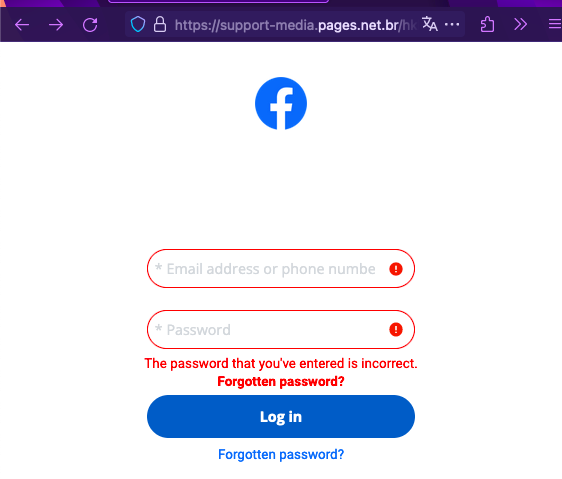
Digging into it, I opened the Firefox dev tools and noted the URL to which the form was sending the login data. I also made a copy of the JSON payload, i.e. the format of the login data expected by the server.
Peering into the depths...
Note it is in Portuguese - "titulo", "valor". Apparently Facebook has been outsourcing to Lisbon.
Then I thought I'd give them some help. I wrote a Perl script that will randomly generate plausible email addresses and rude passwords, then send one "login" every second to the server.
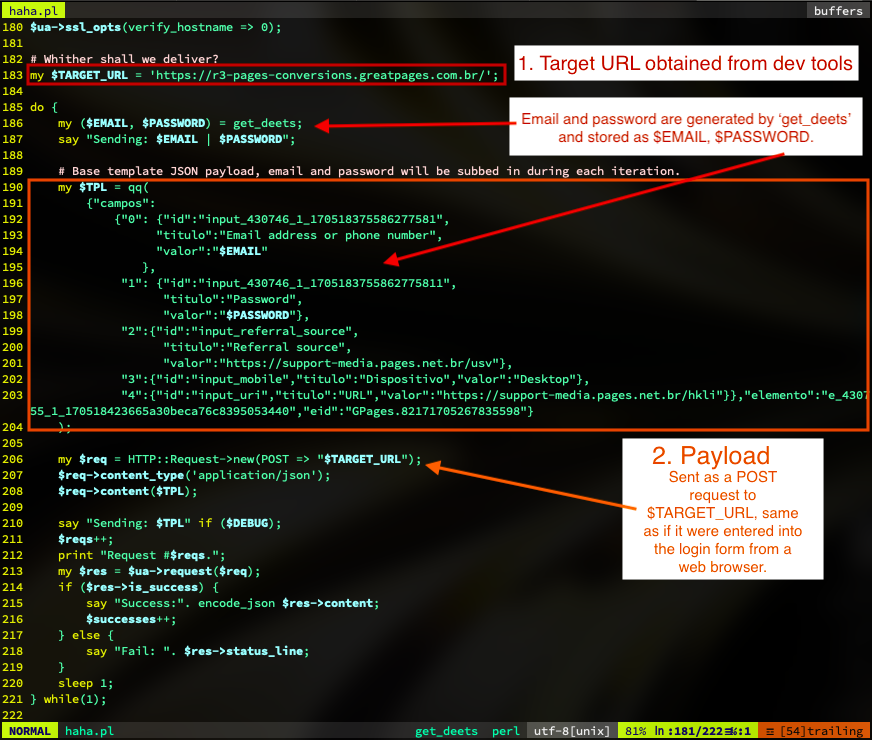
Behold, my Perl!
If you follow the annotations, the same target URL where the login form sends the username and password have been entered into the script.
But that wasn't enough. I thought to brighten up their day, it would be funny for there to be a one in ten chance of sending a selected copypasta. I added some of my favourites to the top of the script, as well as other famous speeches that inexplicably came to mind.
So in addition to the random email addresses, the login form was bombarded with the copypastas of Gorilla Warfare, Rick and Morty, They targeted gamers and Richard Stallman's interjection. It also routinely sent Donald Trump's wall speech, Nixon's watergate speech, Alex Jones' frog speech, and some Sumerian poetry.
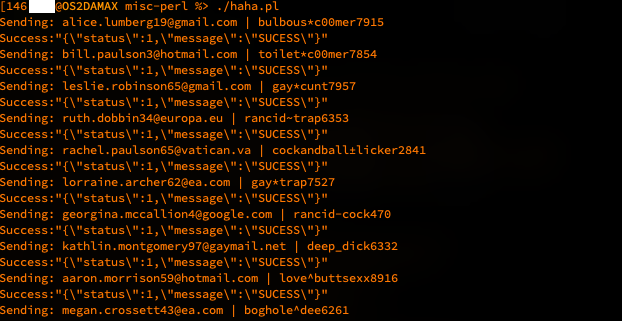
Surely some of these are valid?
Running the script, we see it working. The server replies 'SUCESS' to each submission, even after receiving the very long copypasta texts. I wonder if that's a typo, or just Portuguese. I'm not bothered enough to look it up.
Naturally after 10,000 iterations of this - 9 email addresses and passwords, then 1 pasta - I thought that was enough. Surely the spammer would enjoy some of his own art returned.
And indeed, a week later I visited the same login form to find this message:
____ ____ _____ _ _____ ____ _ _ ____ _____ ____ ____ _ / ___| _ \| ____| / \|_ _| / ___|| | | |/ ___| ____/ ___/ ___|| | | | _| |_) | _| / _ \ | | \___ \| | | | | | _| \___ \___ \| | | |_| | _ <| |___ / ___ \| | ___) | |_| | |___| |___ ___) |__) |_| \____|_| \_\_____/_/ \_\_| |____/ \___/ \____|_____|____/____/(_)
Download haha.pl
If you are inclined to see the script in its entirety, you may download haha.pl here. It isn't my tidiest or cleverest Perl, but it is obvious enough what it does. You'll need the LWP module for it to run.
Addendum - why do this?
The message was an obvious attempt to steal my login details, as well as the login details of countless others. Likely, the scammer would lock the page and charge money to retrieve access. He could use my account to spam others. Or he could sell my details and have someone else use them for identity fraud. Countless possible sins come to mind.
Thus by flooding his database with 10,000 useless usernames and passwords, the whole dataset becomes worthless to him. Also it is funny.